There are many products and services on the market today designed to help notify the right people with (hopefully) the right messages in the event of disruption of day-to-day operations.
Yet we in Business Continuity (and Emergency Management, Crisis Management and ITDR) spend little time, money or effort streamlining how we receive intelligence about events that could potentially disrupt our businesses. Why all the emphasis on outgoing information yet so little on incoming intelligence?
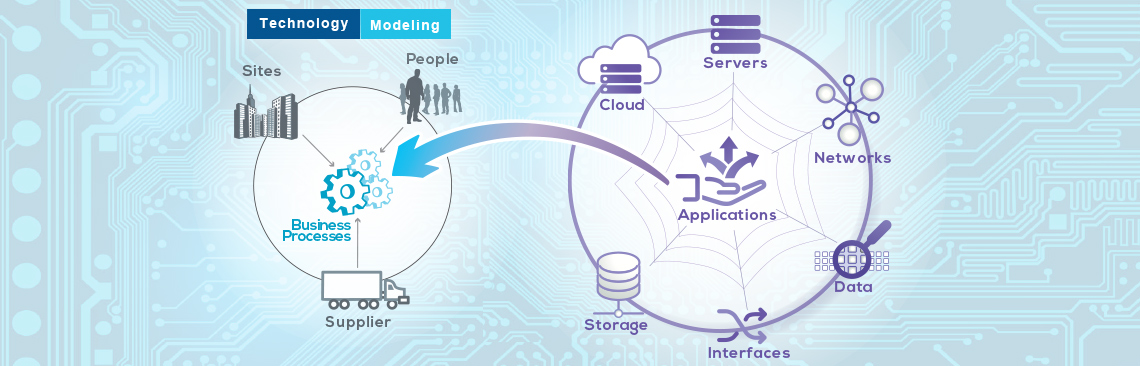
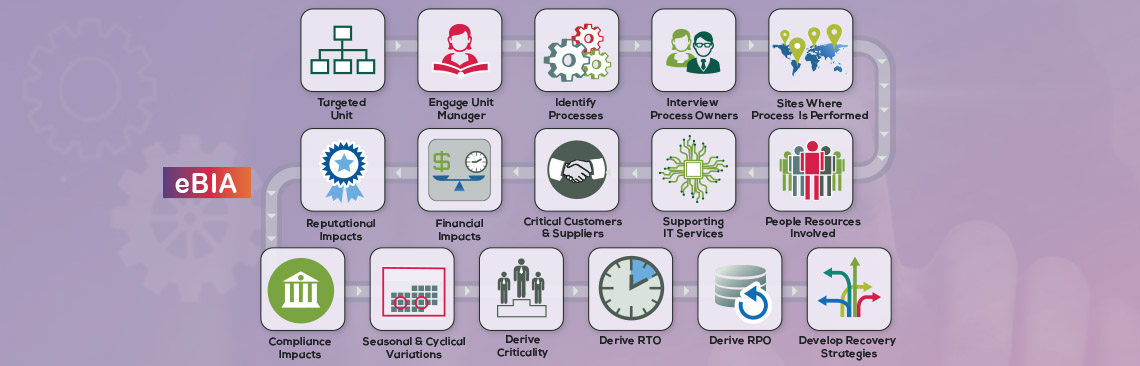
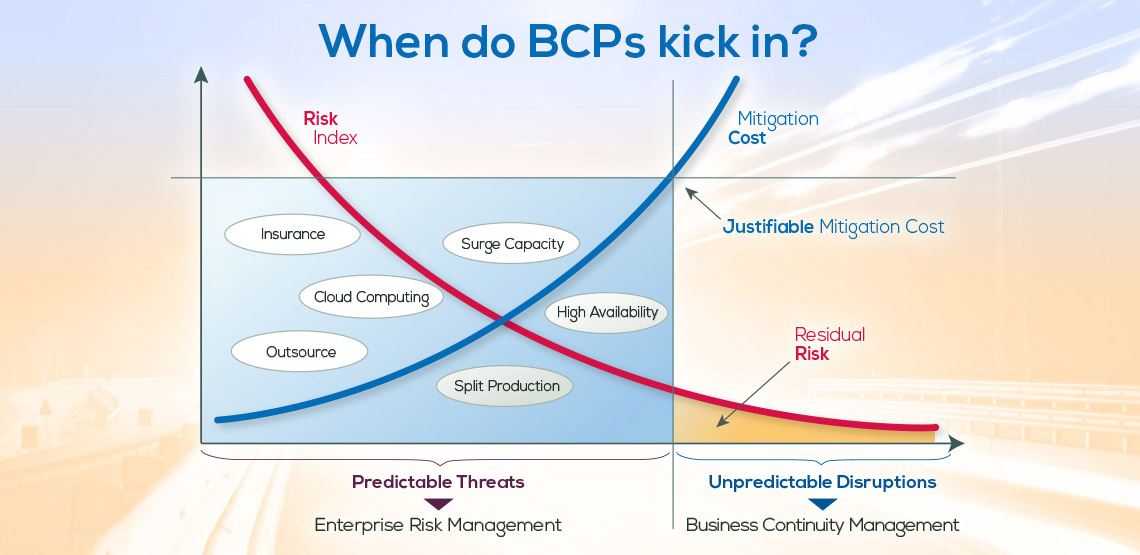
We already know what kind of intelligence we should be anticipating. After all, successful Business Continuity Management and Risk Management uncover knowledge of events that may negatively impact day-to-day operations. And there are many readily available sources which can alert us to those potential, impending or current events for both personal and business use.
- Weather forecasts and alters from national and global sources
- Local alerts from governments and public services
- Internal business alerts from security, facilities and IT monitoring sources
- News feeds – global, regional, local, industry and company-specific – available online
- Filtered news sources refined by 3rd parties to customer specifications
- Social media (especially Twitter and Facebook)
- Help Desk inquiries
These sources of “situational intelligence” could prove immensely valuable, if only we knew how to harness them to make sense of the sheer volume of those streams of information.
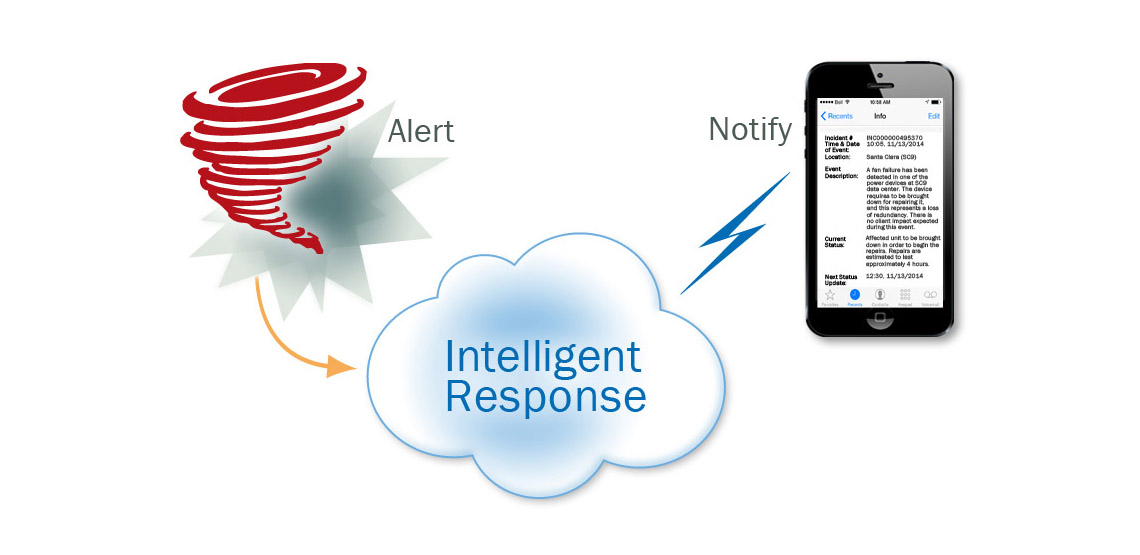
Situational intelligence can provide a real-time (or at least near-real-time) perspective on what is happening in or near our critical facilities, technology infrastructure, workforce and supply chains. But the volume of raw data isn’t useful until it can be filtered to focus on threats to our own narrow operations. There are providers, applications and websites that will help do that. But that’s still only part of the problem.
There are so many ‘threats’ to consider: supply chain issues, customer concerns, infrastructure problems, weather patterns, transportation interruptions, geophysical disruptions, plus both local, regional and even international societal concerns. Then there are internal threats emanating from our technology, facilities, workforce, and a long list of other actions and activities that may disrupt normal operations.
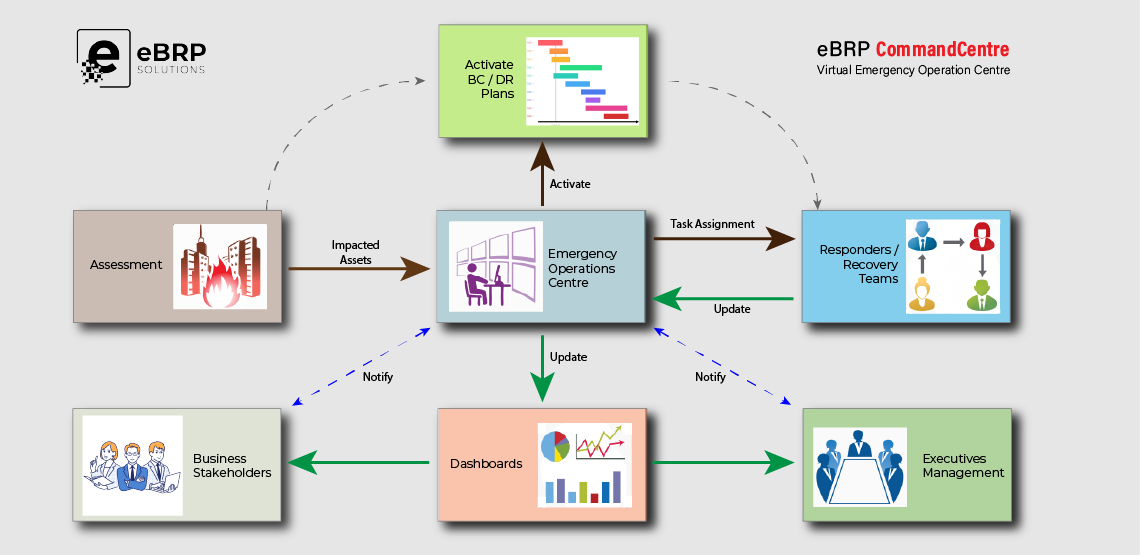
Intelligence about these potential threats may come in from many sources through a variety of means – radio, RSS, direct feeds, phone calls, emails, tweets, software alerts, etc. Often, those sources are monitored by different departments or individuals. What may impact the recipient of one alert may also impact other business operations. But that situational intelligence doesn’t always flow down to those audiences on a timely basis. Sharing situational intelligence – making certain that important alerts and updates reach all the right audiences – has a unique set of requirements:
- A centralized ‘clearing house’ capable of understanding operational risks across the organization
- Operating rules to filter incoming intelligence (either automatically or manually) to target those alerts with real potential impact
- Knowledge of which business processes and operations could potentially be impacted by which types of intelligence and/or threats
- Means to notify specific teams or individuals (representing those potentially-impacted functions) quickly
- Capability for notified teams or individuals to access, assess and validate relevant situational intelligence to determine what actions – if any – should be taken.
Could you build a system – online, accessible and largely automated – to aggregate, filter and notify those who could benefit from alerts to specific organizational threats? Possibly; but luckily, you don’t have to build one. eBRP Solutions has already built one for you: ProACT, our new first step in Service Continuity Management.
Take your Business Continuity, Service Management and Risk Management programs into the future of Situational Intelligence. Let eBRP show you how.